
Security for Agent Connectors: least privilege, injection resistance, and safe toolchains
In 2025, the riskiest part of “agentic” systems isn’t the model — it’s the connectors. This month is a practical playbook for securing tools: least privilege, prompt-injection resistance, safe side effects, and auditability that holds up under incident response.
Axel Domingues
In March I called it the Compliance Cliff: the moment you stop demoing agents and start connecting them to real systems is the moment governance becomes a survival skill.
In April we saw agent runtimes emerge — SDKs, orchestration primitives, traces.
In May we hit the 1M-token era — and learned that context is now a budget and an attack surface.
In June and July we treated agents like distributed systems and multi-agent org charts.
So August is where the rubber meets the road:
Tools. Connectors. Credentials. Side effects.
Because the ugly truth is:
You can have a “safe” model and still ship an unsafe system…
if your connectors behave like a root shell with a friendly chat UI.
This article is a practical security playbook for agent connectors — focused on controls that teams can actually ship.
email, Slack, Jira, CRM, databases, cloud APIs, payment providers, internal admin endpoints, CI systems, file stores, browsers, and “just a webhook”.
The core idea
Treat connectors as a capability boundary, not a convenience API.
The core risk
A prompt injection is just a social engineering attack on your toolchain.
The core control
Least privilege + policy + validation at the connector boundary.
The outcome
You can ship agents that are auditable, reversible, and boring.
The Connector Threat Model (the one people skip)
Traditional apps have clear trust boundaries:
- user input is untrusted
- backend is trusted
- DB is trusted
- privileged credentials live server-side
Agentic apps blur those boundaries because the model:
- consumes untrusted content (web pages, emails, PDFs, tickets, chat)
- produces actions (tool calls) that cause side effects
- is vulnerable to manipulation (prompt injection, jailbreaking, data exfiltration)
- is non-deterministic (the same input can behave differently)
So the right mental model is not “LLM security.”
It’s:
Your agent is an untrusted process that can ask for power.
Your job is to make sure it can’t get more power than it should.
The three attacker goals
Exfiltrate data
Get secrets, PII, internal docs, or tenant data out through outputs or tool calls.
Escalate privileges
Trick the system into using a more powerful connector, scope, or identity.
Cause side effects
Send emails, delete records, issue refunds, change ACLs, create users, push code.
Poison the loop
Write bad state (tickets, notes, docs) that later becomes “trusted context”.
If you secure for those four, you’re already ahead of most teams.
Prohibited Practices (the “we’ll fix it later” cliff)
These are not theoretical. They are what breaks in the first incident review.
Smell: a single “SERVICE_API_KEY” that can read and write across every tenant, system, and environment.
Why it’s fatal: once the agent can reach that key (directly or indirectly), your blast radius is global.
Smell: the model emits a string like "DELETE FROM users WHERE ..." or "curl ..." and you execute it.
Why it’s fatal: this is code injection — but with a probabilistic generator as the attacker.
Smell: a connector that can “search and update” in one call, or a “do-anything” admin endpoint.
Why it’s fatal: you can’t apply selective friction (confirmations, approvals, rate limits) when reads and writes are mixed.
Smell: whatever the web page says gets promoted into system state, tickets, or knowledge bases without verification.
Why it’s fatal: tool outputs are untrusted inputs. They can contain injections, malware links, or subtle misinformation.
Smell: you can’t answer “who did what, when, with what inputs, and why?” for a tool call.
Why it’s fatal: you can’t do incident response, compliance, or root-cause analysis without a forensic timeline.
Those practices tend to appear because teams think of connectors as “integrations.”
But connectors are privileged execution surfaces.
So let’s build them like we build payment flows: carefully.
The Connector Boundary Pattern (the control that actually ships)
If you only take one architectural idea from this month, take this one:
Connectors do not live inside the agent.
They live behind a boundary that enforces identity, policy, validation, and logging.
I like to name that boundary the Connector Gateway (or Tool Proxy).
It has four jobs:
- Auth brokerage: mint short-lived, scoped credentials per run / per tenant / per user
- Policy enforcement: allow/deny + require approvals based on risk and context
- Input validation: schema validation, type checks, safe defaults, and hard limits
- Audit + telemetry: immutable logs, traces, and security signals
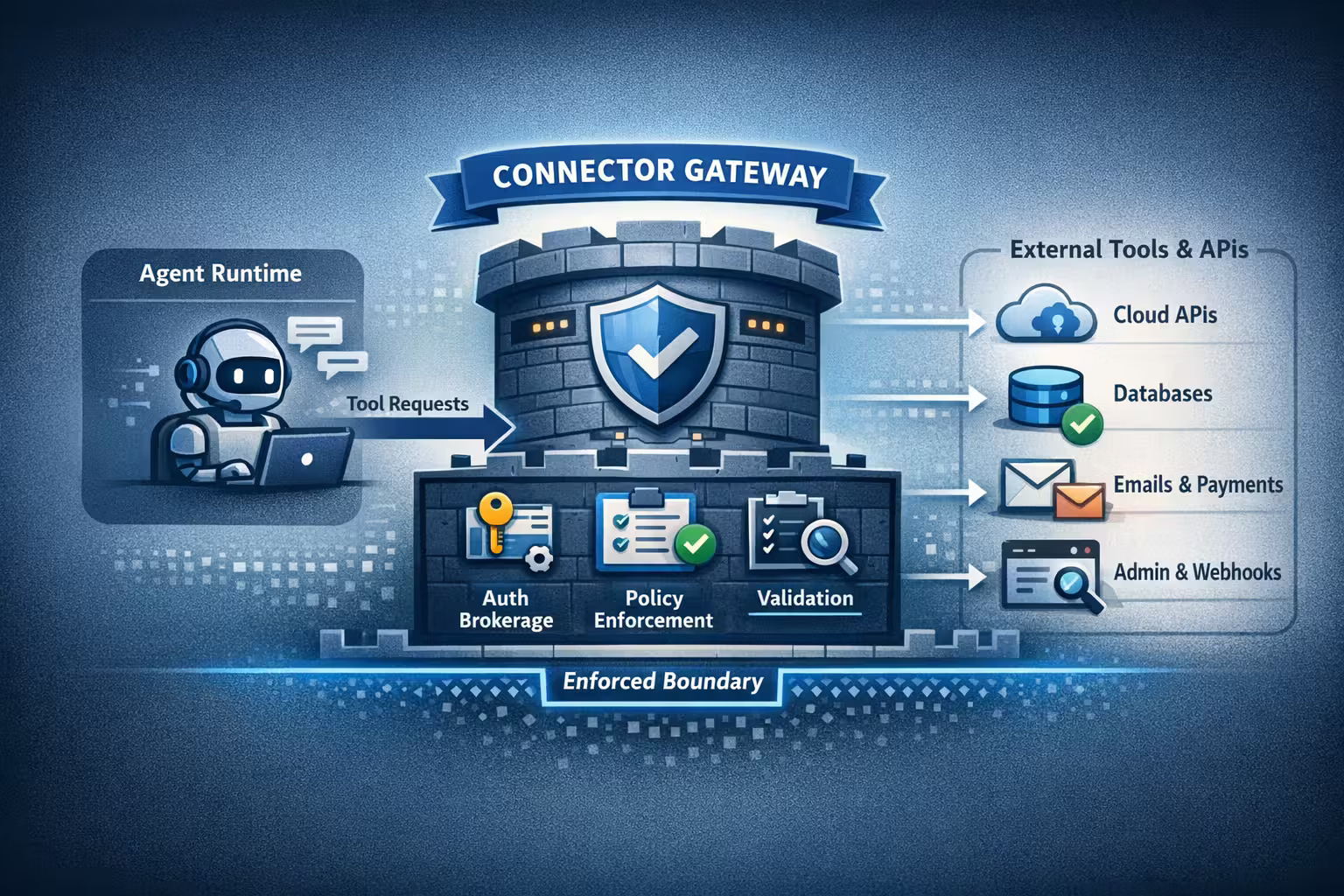
If tools are invoked directly from an agent runtime, you inevitably end up with one privileged credential and no consistent enforcement point.
Least Privilege for Tools (practical, not aspirational)
Least privilege is easy to say and hard to ship because it forces you to answer:
- whose identity is this tool acting as?
- which tenant, project, or workspace?
- for how long?
- with what scope?
- with what rate limits and side-effect budget?
So treat least privilege as a token-minting problem.
Rule 1: Every tool call must have an identity
Not “the service.”
A real principal:
user:<id>for user-initiated runssystem:<workflow>for scheduled runsagent:<bot>for internal assistants
And that principal must map to a policy.
Rule 2: Make scopes boring and composable
Instead of crm:admin, create scopes like:
crm:contacts.readcrm:contacts.writecrm:deals.readcrm:deals.write
Then make “write” scopes require more friction.
Rule 3: Prefer ephemeral credentials
- short TTL
- refreshable
- revocable
- constrained to tenant + principal
If your agent uses long-lived credentials, you’ve already lost the benefit of fine-grained controls.
The golden rule
A tool credential should expire faster than your incident response starts.
The reality check
If revoking a tool credential takes hours or days, you don’t have “controls” — you have hope.
Injection Resistance (treat content as hostile)
Prompt injection isn’t magic.
It’s the oldest attack in software:
“Make a privileged system do something it shouldn’t… by feeding it convincing text.”
In agent systems the attacker doesn’t need code execution. They need instruction execution.
So the key design move is:
Separate “content” from “control”
- Content is untrusted: emails, pages, docs, tool outputs
- Control is trusted: system prompts, policies, tool schemas, allowlists
If you let content write control, you’re building a remote-control backdoor.
The connector-side rules that matter
- The model can propose; the gateway disposes
- Tool inputs must be structured and validated
- Tool outputs must be treated as untrusted input
- Side effects require friction proportional to risk
Here’s what “structured” really means: your tool interface should make unsafe requests impossible.
{
"tool": "send_email",
"args": {
"to": ["customer@example.com"],
"subject": "Your quote",
"body_markdown": "...",
"attachments": [
{ "file_id": "doc_123", "name": "quote.pdf" }
]
}
}
Not:
Send an email to the customer with the attached quote and ask them to wire money to this new account.
The difference is everything: structured inputs give you enforcement hooks.
If you do, your connector becomes a prompt interpreter — which is a second model, but without safety features.
Safe Toolchains (side effects without fear)
A secure connector isn’t just “auth + allowlist.”
It’s a toolchain that makes side effects:
- idempotent
- rate limited
- reviewable
- reversible when possible
- auditable always
This is where June’s “eventually correct” thinking comes back:
Side effects need a transaction model
For write tools, I strongly recommend a two-phase pattern:
- Plan: the agent proposes an action (what + why)
- Commit: the system executes it with policy checks + optional approval
That can look like:
- staged drafts (email drafts, Jira drafts, PR drafts)
- dry-runs for infrastructure changes
- “preview diff” for DB updates
- hold-to-confirm for payments/refunds
It’s to make “unsafe irreversible writes” require deliberate gates, while safe reads and safe drafts stay fast.
A simple risk ladder that works
- Read-only → no human required, minimal friction
- Write-draft (creates a draft artifact) → allowed with logging
- Write-commit (irreversible or costly) → requires approval / second factor / workflow gate
Observability: security you can debug
Security controls that can’t be observed don’t exist.
Your connector boundary should emit a complete forensic trail:
- tool name + version
- principal identity + tenant
- request args (redacted as needed)
- policy decision (allow/deny/require-approval)
- latency + retries
- outcome (success/failure) + error class
- correlation IDs linking: prompt → tool call → downstream request → state change
I like to treat tool calls as first-class spans in tracing:
Trace it
Every tool call is a span with inputs, decision, outcome.
Audit it
Every side effect produces an append-only audit event.
And then you add detection on top:
- spikes in denied calls
- repeated attempts to access write tools
- abnormal destinations (new domains, new recipients)
- unexpected data volume (exfil attempt signal)
- tool-call loops (agent stuck, or being manipulated)
A Build Plan You Can Ship in a Quarter
This is a “doable” implementation sequence that produces real risk reduction early.
Step 1: Inventory tools and classify risk
Make a registry with:
- owner
- read/write classification
- blast radius (tenant / system / global)
- reversibility
- PII exposure
- external egress (yes/no)
Step 2: Put every connector behind one gateway
Even if it’s thin at first:
- one auth layer
- one logging pipeline
- one place to enforce schema validation
Step 3: Add per-tool schemas and hard limits
- required fields
- max lengths
- allowlisted enum values
- max number of recipients/items/records
- denylist patterns for high-risk strings
Step 4: Implement token minting + short TTL
- per-tenant
- per-principal
- per-tool scopes
- revocation path that’s tested
Step 5: Add policy decisions + friction
- write tools require confirmations
- high-risk tools require approvals
- rate limits by principal + tenant
Step 6: Red-team for injection and exfil
- malicious web pages
- hostile emails
- poisoned tickets
- tool output carrying hidden instructions
- observability,
- input validation,
- and a single enforcement point.
Implementation Notes (what teams usually miss)
1) “Tool allowlisting” is not enough
Allowlisting tool names helps. But the real danger is arguments.
You must validate arguments, enforce limits, and apply policy to the intent of the call.
2) Your gateway needs an egress policy
If your agent can browse the web or call arbitrary URLs, you need:
- DNS/domain allowlists where appropriate
- outbound proxying
- logging and limits on external calls
Otherwise your agent becomes a data exfiltration machine.
3) Store “what the agent saw” for investigations
If you can’t reproduce:
- the prompts,
- the retrieved context,
- the tool outputs,
- and the policy decisions…
…you can’t prove what happened.
(And you can’t fix it confidently.)
4) The model is not your policy engine
Models can help propose actions. They cannot be trusted to enforce policy.
Policy enforcement must happen outside the model — deterministically.
Resources
OWASP Top 10 for LLM Applications (tool & connector risks)
A practical threat taxonomy for agent systems: prompt injection, insecure output handling, excessive agency, data leakage — the exact failure modes your connector gateway is meant to contain.
NIST SP 800-63B — Digital Identity Guidelines (auth sessions & MFA)
Useful for making “every tool call has an identity” real: session assurance, re-auth triggers, MFA guidance, and how to think about identity at the boundary.
FAQ
No. You need risk-based friction.
Reads should be fast. Draft writes should be easy. Irreversible writes should be gated.
If approvals are too broad, teams will bypass them — and you’ll end up less safe than before.
Make tenant identity a first-class field in your gateway and tokens:
- every request is scoped to one tenant
- every tool token is minted for one tenant
- every log event includes tenant + principal
Treat “cross-tenant access” as a policy violation by default.
Wrap them.
If the external system only offers coarse permissions, your gateway can still enforce:
- allowlisted operations
- argument constraints
- rate limits
- approvals
- audit logs
You can’t fix the upstream API, but you can contain it.
You can’t prevent malicious text from existing.
You can prevent malicious text from causing privileged side effects by:
- keeping control separate from content,
- validating tool calls,
- enforcing policy outside the model,
- and limiting privileges.
That’s “solvable enough” to ship responsibly.
What’s Next
August was about securing the hands of the agent — the connector layer where side effects happen.
Next month, the lens widens to governance timelines and obligations:
GPAI Obligations Begin: what changes for model providers and enterprises
Because once your connectors are safe, the next question becomes:
What do you need to prove — and to whom — when regulators, customers, and auditors start asking?
GPAI Obligations Begin: What Changes for Model Providers and Enterprises
The EU AI Act turns “model choice” into a regulated interface. This month is a practical playbook: what GPAI providers must ship, what enterprises must demand, and how to build compliance into your agent platform without slowing delivery.
Multi-Agent Systems Without Chaos: supervisors, specialists, and coordination contracts
Multi-agent setups don’t fail because “agents are dumb.” They fail because we forgot distributed-systems basics: authority, contracts, budgets, and observability. This month is a practical architecture for scaling agents without scaling chaos.