Voice Agents You Can Operate: reliability, caching, latency, and human handoff
Voice turns LLMs into real-time systems. This month is about building voice agents that meet latency budgets, degrade safely, and hand off to humans without losing context—or trust.
Axel Domingues
Text chat lets you hide a lot of sins.
Voice does not.
The moment you ship a voice agent, your system becomes a real-time pipeline:
- audio in
- partial transcripts
- tool calls
- streaming tokens
- audio out
- and a human who will interrupt you mid-sentence if you’re slow or wrong
So this month I’m treating voice agents like what they actually are:
distributed, stateful, latency-budgeted systems.
Not “a model with a microphone.”
The focus here is operational architecture:
- latency budgets
- failure modes
- caching
- reliability controls
- and human handoff as a first-class workflow
The goal this month
Build voice agents that feel responsive, stay safe under failure, and are operable by on-call humans.
The hard truth
Voice is a latency game.
If you can’t hit the budget, no amount of “smart” will save you.
The reliability lens
Treat every connector and model call as unreliable I/O and design graceful degradation.
The non-negotiable
Handoff is not a failure mode.
It’s a product feature with architecture behind it.
Why Voice Agents Break Differently Than Chat
Text agents fail like software. Voice agents fail like phone calls.
When an LLM is “thinking” in text, the user waits. When an agent pauses in voice, the user assumes the line is dead.
This changes everything:
- Latency is UX. Every 200ms matters.
- Turn-taking is correctness. Interruptions (barge-in) are normal.
- Silence is an error state. You need “I’m here” behaviors.
- Confidence must be explicit. If you’re not sure, you must sound not sure.
- Handoff must preserve trust. The user expects continuity, not “start over.”
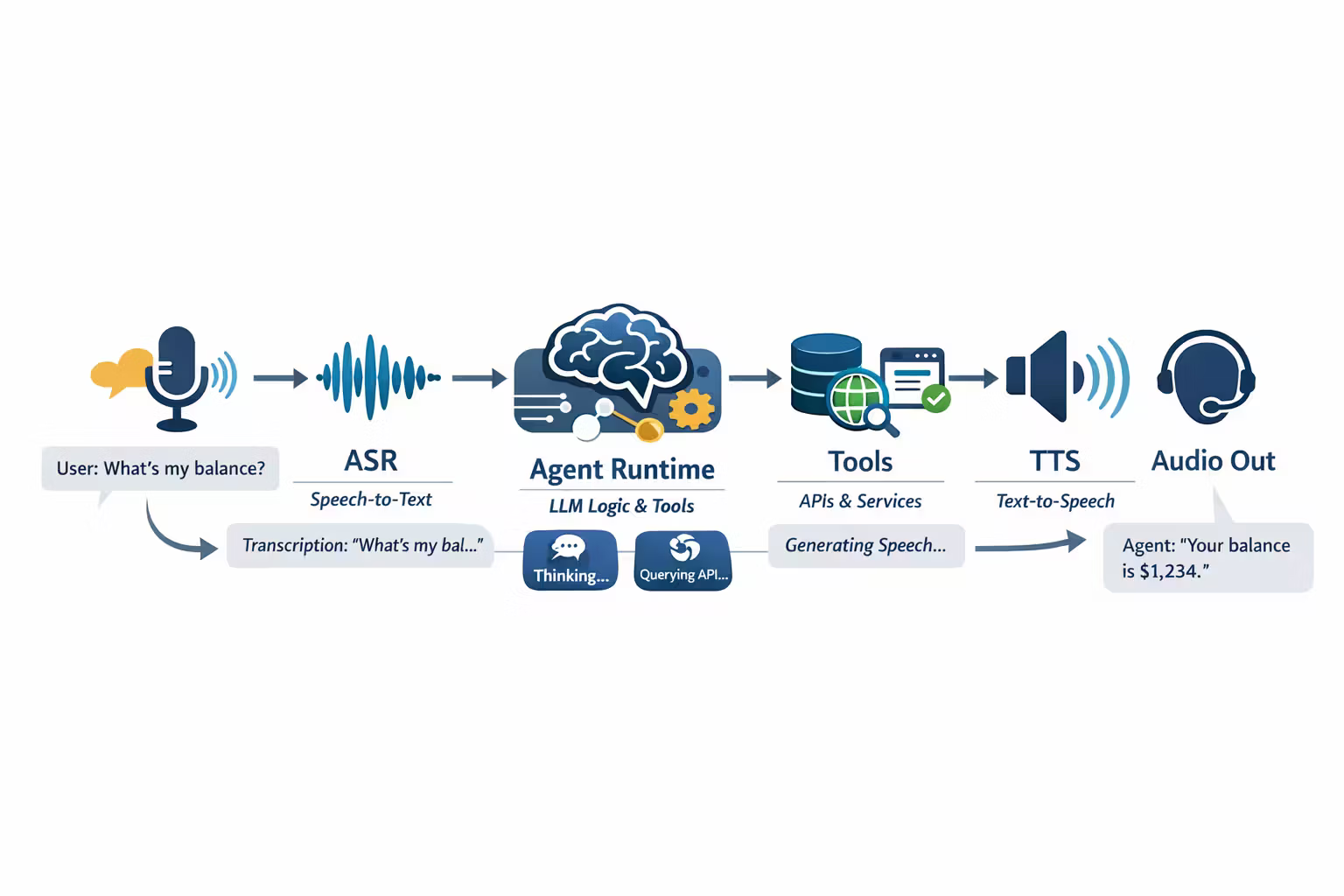
The Latency Budget: Start With the Stopwatch, Not the Model
A voice conversation has an intuitive rhythm:
- The user stops speaking.
- The assistant responds quickly enough that it feels like a human is there.
If you don’t design for this rhythm, you will ship something that feels broken even when it is “accurate.”
A practical budget
Your exact budget depends on your domain, but a good starting point is:
- Time-to-first-response (TTFR): “assistant starts speaking” within ~1 second after the user finishes
- Time-to-first-token (TTFT): model starts streaming quickly (you feel it in the audio)
- Sustained throughput: no long gaps mid-sentence
- Recovery time: if something fails, say something within the same budget (even if it’s a fallback)
If you need more time, speak:
- “Got it — let me check that.”
- “One moment while I look that up.”
- “I’m pulling your account now.”
Where latency actually comes from
Voice latency is the sum of many parts:
WebRTC jitter, mobile radio variance, buffering, and codec decisions can add real delay.
Batch ASR is slow. Streaming ASR with partial hypotheses is what makes real-time interaction possible.
The model is rarely the only call. The slowest connector dominates your user’s perception.
High-quality voices cost time. Streaming TTS matters as much as streaming tokens.
Serialization, logging, tracing, prompt assembly, and network hops can be death-by-a-thousand-cuts.
The Architecture: A Duplex Pipeline With Stateful Control
If you want voice to feel natural, you need simultaneous input + output:
- input keeps arriving (user interrupts, background noise, corrections)
- output streams continuously (assistant speaks, but can be cut off)
A good mental model is a duplex pipeline with explicit state machines.
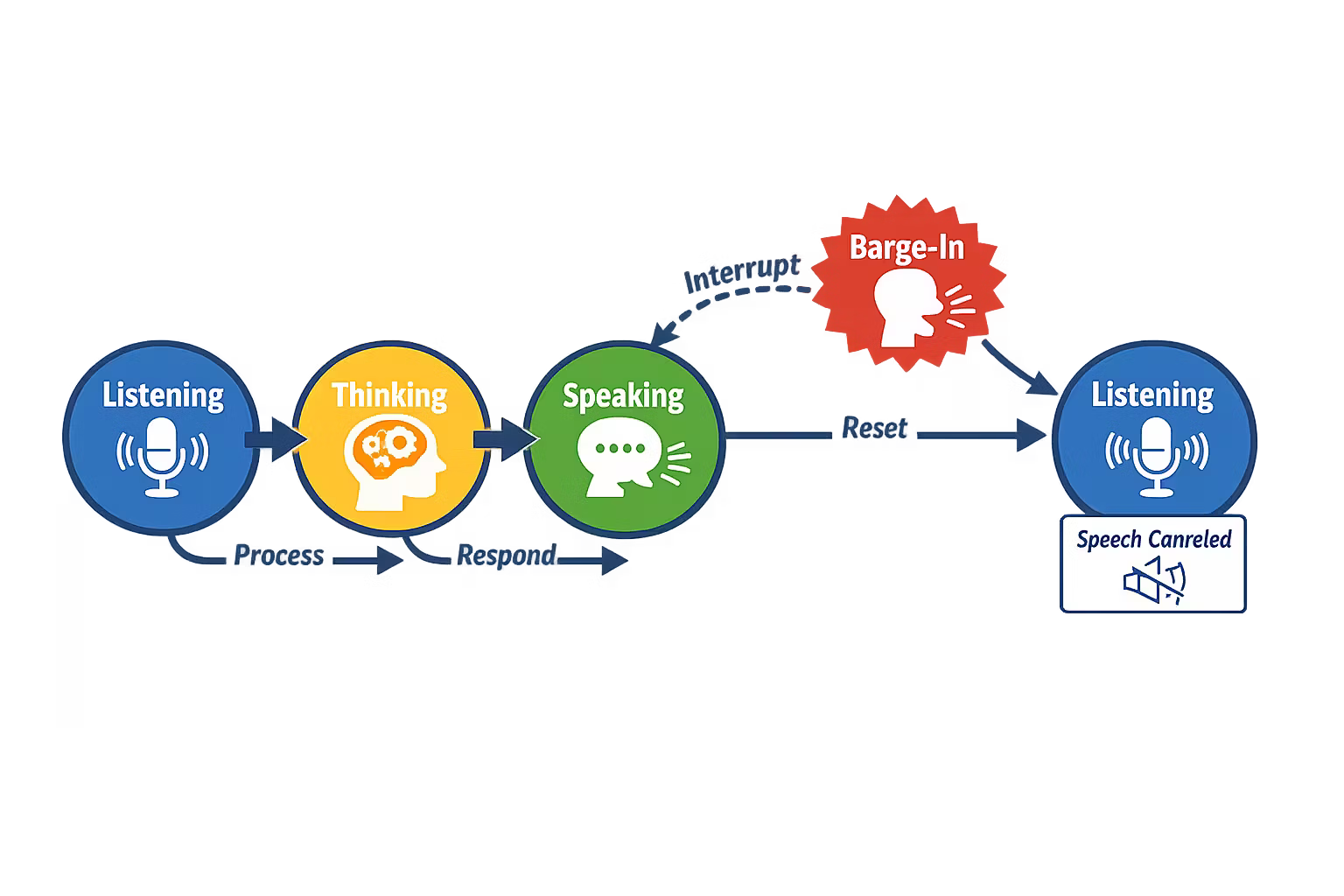
The three state machines you need
Most teams only build one. Operable systems build all three:
Conversation state machine
Listening / Thinking / Speaking / Handoff / Ended, with explicit transitions.
Audio state machine
Capture / VAD / stream / buffer / drop / reconnect, with jitter handling.
Tooling state machine
Plan / call / retry / timeout / fallback / redact / audit, per connector.
Safety state machine
Policy checks, injection filters, action gating, and “safe response” behaviors.
Voice makes implicit state visible.
Reliability: Design for Cancellation, Timeouts, and Partial Truth
Voice agents must handle two hard realities:
- Users interrupt (barge-in).
- Everything external fails (ASR, LLM, tools, TTS, network).
The reliability move is to treat every stage as cancelable and bounded.
Cancellation is a feature, not an edge case
When the user starts speaking while the agent is speaking:
- stop TTS playback immediately
- cancel the current LLM generation (or at least ignore the remainder)
- invalidate any “planned” tool calls that no longer match the user’s intent
- restart the loop with the new utterance as the highest priority
If cancellation only happens in the UI, you’ll still:UI → audio output → model stream → tool calls
- pay for tokens
- trigger side effects
- and log nonsense conversations
Timeouts and fallbacks: the 3-tier rule
For every external call, define:
- Soft timeout: “speak something” and keep working
- Hard timeout: stop waiting, switch to fallback path
- Fail-closed boundary: never perform side effects after you’ve lost certainty
Example:
- “I’m checking that now…” (soft timeout)
- “I can’t reach the service right now — I can connect you to someone.” (hard timeout)
- “No refunds issued” if you didn’t confirm account identity (fail-closed)
Prefer a controlled fallback over silent correctness.
Caching: The Only Way to Buy Both Speed and Cost
Caching in voice is not just “performance optimization.” It’s a product requirement.
You cache for three reasons:
- speed (hit the latency budget)
- cost (voice turns can be frequent and long)
- reliability (serve something useful when dependencies fail)
Four caches that actually matter
Prompt assembly cache
Reuse system prompts, policy blocks, tool schemas, and static context across turns.
Semantic response cache
If the user asks a repeatable question, serve a validated answer template fast.
TTS audio cache
Cache common phrases (“One moment…”, “I can help with that…”) as audio snippets.
Connector result cache
Cache tool results with strict TTLs (and per-tenant scoping) to avoid repeated slow calls.
A safe caching rule: cache structure, not secrets
What you cache depends on risk:
- Safe: public FAQs, help texts, “status page” responses, generic confirmations
- Dangerous: anything with personal data, account details, or sensitive tool outputs
If you cache sensitive tool results, you need:
- per-user / per-tenant keys
- strict TTLs
- encryption at rest
- and auditability
In voice, people overshare.
Your caches will become your breach surface.
Streaming Strategy: Don’t Wait for the Perfect Sentence
A voice agent that waits for the model to finish is dead on arrival.
You want:
- streaming ASR → partial hypotheses
- streaming LLM → early tokens
- streaming TTS → speaking while generating
But you also want correctness.
So you need a strategy for partial truth.
The “two-layer speech plan”
Split output into two layers:
- Low-risk scaffolding (fast, cached, generic)
- High-risk facts (slow, verified, tool-backed)
Example:
- Layer 1: “Okay — I’m pulling up your order.”
- Layer 2: “Your order #1234 shipped yesterday and arrives Friday.”
This gives you responsiveness without hallucinating facts.
- the agent always acknowledges immediately
- facts arrive only when verified
- and the user never sits in silence
Human Handoff: The Architecture of “I’ll Get Someone”
Most teams treat human handoff like a UI button.
Operational teams treat it like a workflow with guarantees.
Handoff has three requirements:
- Continuity: the human sees context and doesn’t ask the user to repeat themselves
- Bounded risk: once you hand off, the agent must stop making side effects
- Auditability: you can explain why handoff happened
The handoff packet
A good handoff packet is small, structured, and safe.
It usually includes:
- session id + user id (or anonymous token)
- last N turns (redacted)
- current intent classification
- tool call history (names, durations, success/failure, redacted payloads)
- extracted entities (order id, plan type, error codes)
- reason code for handoff (timeout, low confidence, policy boundary, user request)
If the human can’t understand the situation in 10 seconds, your handoff is not real.
When to trigger handoff
You should have explicit policies, not vibes:
Immediate handoff. Don’t argue. Voice is not the place for persuasion.
If you can’t verify identity or confirm the invariant, fail closed and route to a human.
If you hit the same error twice, stop retrying and hand off with a reason code.
If tool calls repeatedly violate budgets, the system should degrade toward human assistance.
A Practical Build Recipe
This is the minimum set of design moves I’d require before calling a voice agent “production.”
Define your latency SLOs and measure them per stage
Track:
- TTFR (speech start)
- ASR partial latency
- model TTFT + tokens/sec
- tool call p95/p99
- TTS start latency
- end-to-end turn duration
Build explicit cancellation into every stage
Support:
- barge-in cancellation
- connector cancellation (or “ignore late results”)
- idempotency for side-effecting tools
Add a cache hierarchy that respects risk
Implement:
- prompt assembly cache
- safe semantic cache
- TTS snippet cache
- connector cache with TTL + scope
Create “safe speech scaffolding”
Speak early with low-risk phrases. Delay facts until verified by tools or deterministic sources.
Make handoff a workflow, not a button
Produce a handoff packet. Stop side effects. Expose reason codes. Ensure continuity for the human.
Ship with runbooks and circuit breakers
When dependencies degrade:
- reduce tool usage
- switch to cheaper/faster models
- fall back to FAQ mode
- escalate to human
Observability: Your Voice Agent Needs a “Conversation Trace”
If you can’t replay what happened, you can’t improve it.
A useful trace looks like this:
- audio timeline (segments, interruptions, silence)
- ASR hypotheses over time
- agent decisions (state transitions)
- prompt version + tool schema version
- tool calls (latency, success/failure, redacted inputs/outputs)
- TTS segments played (including cancellations)
- handoff reason code (if triggered)
The metric that matters
Silence time.
Measure how long the user experiences no audio output after they stop speaking.
This is the “rage quit” predictor.
Failure Modes to Expect (So You’re Not Surprised)
Cause: missing barge-in cancellation, slow VAD, or buffering.
Fix: lower output buffer, cancel TTS immediately, improve VAD tuning.
Cause: soft timeouts without hard timeouts.
Fix: enforce hard timeouts and route to fallback/handoff.
Cause: waiting for full sentences before speaking.
Fix: streaming + two-layer speech plan + cached scaffolding.
Cause: speaking high-risk facts before verification.
Fix: tool-backed facts only, or explicitly qualify uncertainty.
Cause: no conversation trace or no reason codes.
Fix: structured logs, stage timings, and deterministic handoff packets.
Resources
WebRTC 1.0 (W3C) — real-time media in browsers
The canonical spec for browser-based real-time audio/video: the foundation for low-latency voice transport, jitter handling expectations, and integration patterns.
RFC 8825 — Overview of WebRTC
A practical map of the WebRTC protocol suite (ICE/DTLS/SRTP/data channels), useful when you’re debugging “why is latency/cancellation weird?” across layers.
FAQ
If you want natural voice UX, yes—at least for the user-facing edges:
- streaming ASR so you can react quickly
- streaming TTS so you can start speaking early
- streaming LLM output so you can avoid long pauses
Internally, you can still run batch tool calls, but the user should experience continuous feedback.
Usually, yes.
Voice gives you less room to display uncertainty, sources, or disclaimers. That means you should:
- restrict tool permissions
- prefer deterministic flows for high-risk actions
- and escalate to humans earlier when confidence drops
Cache what is:
- static (prompt blocks, tool schemas)
- public (FAQs)
- generic (TTS snippets)
- time-bounded (connector results with TTL)
Avoid caching personalized or sensitive content unless you have explicit compliance and audit controls.
By treating handoff as an engineered workflow:
- the agent explains what’s happening (“I’m connecting you now…”)
- the human receives a structured handoff packet
- the user doesn’t repeat themselves
- and the agent stops side effects the moment handoff begins
What’s Next
October was about making voice agents operable:
- latency budgets you can defend
- caches that buy speed without buying risk
- reliability controls that handle interruption and failure
- and handoff as a first-class architecture feature
Next month I zoom out from voice into the thing that makes all agent products scalable:
The Connector Ecosystem: MCP adoption patterns, versioning, and governance
Because once you can run one agent safely… the next challenge is running a hundred connectors without turning your platform into chaos.
The Connector Ecosystem: MCP adoption patterns, versioning, and governance
Once agents can call tools, connectors become the new platform surface. This month is a playbook for adopting MCP at scale: patterns that work, versioning that doesn’t break customers, and governance that keeps the ecosystem sane.
GPAI Obligations Begin: What Changes for Model Providers and Enterprises
The EU AI Act turns “model choice” into a regulated interface. This month is a practical playbook: what GPAI providers must ship, what enterprises must demand, and how to build compliance into your agent platform without slowing delivery.